What is SPIT?
SPAM Over Internet Telephony: A billion dollar threat in 2015
SPIT is SPAM Over Internet Telephony. SPIT calls are unsolicited voice or video calls placed using Internet telephony.
Today, the focus of many attackers is to attempt to gain access to customer's VOIP gateways/ITSP trunk and to use this for monetary gain "toll bypass" or "toll fraud". The end game is make calls to the regular telephone network at the victim's expense, potentially running up huge bills in the process. One vendor claims that the total cost of VOIP infrastructure hacking fraud exceeds four billion dollars per annum, worldwide. The cost to victims of individual attacks can run into thousands of dollars.
Where does SPIT come from?
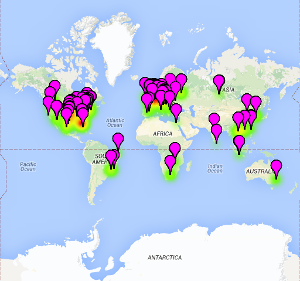
SPIT: A worldwide threat
A few years ago it was claimed that most SPIT attacks came from a few hackers - and much of the blame was laid at the door of Chinese and Palestinian criminals.
Whilst some attacks still emanate from sources in those geographies, today the SPIT landscape appears to be different. Although IP spoofing may cloud the issue, our tracking systems show that SPIT attacks now come from all over the world - and target systems located all over the world.
A very large proportion of recent attacks on servers now originate from within the United States and Europe, meaning that old SPIT defense strategies for businesses operating in the Western hemisphere, such as geolocation based IP blocking, are no longer as effective as they once were.
SPIT is evolving.
What tools and VOIP protocols are used for attack?
No longer a SIP UDP-only problem
For SIP based attacks, UDP based tools based on "Friendly-scanner" (AKA sipvicious), "sipcli" and VaxSIPUserAgent are used to generate the bulk of SIP attacks.
H.323 based attacks are on the rise, with an OpenH323 based tool (claiming to be "cisco" - even though it's quite clearly nothing whatsoever to do with the network equipment vendor) appearing more and more frequently.
Because of the evolving nature of SPIT, in joint H.323/SIP enabled deployments, it is no longer sufficient to disable SIP UDP (although still a helpful protective measure to reduce the volume of attacks in deployments where SIP UDP is not required)